This section displays the claims that will be signed and base64-encoded into a complete JSON Web Token. Signed JSON Web Token Key. Generate 32-byte key; Generate 64-byte key; Generate 128-byte key; Base64-encode the token Copy JWT to Clipboard.
- Generate Jwt Token With Secret Key Online
- Generate Jwt Token With Private Key
- Generate Jwt Token With Private Key Python
Generate Jwt Token With Secret Key Online
This guide describes the Assertion Signing Key specification, how to generate a JSON Web Token (JWT) from the signing key, and how to issue a channel access token v2.1 using the generated JWT.
- JWT tokens are signed using a secret or key selected by the manager of the access profile. JWT tokens are used by identity providers (for example Okta, OneLogin, Auth0) that authenticate users and provide verified access to business applications.
- This tutorial guides you on how to create JWT token and sign with RSA private key. JWT (JSON Web Token) is an encoded representation of a JSON object. JWTs are used in authentication/ authorization mechanisms. Create JWT Token and Sign with RSA Private Key. As mentioned JWT’s are encoded representation of a JSON object.
- I believe the libraries I'm attempting to use in dotnet core are trying to load a cert as an X509 then get the RSA Private key to send into a jwt.Encode method. I am not able to just use the pem file.
# Diagram for issuing a channel access token v2.1
This diagram shows these three steps:
- Create an Assertion Signing Key (Step 1 in the diagram)
- Generate a JWT (Step 6 in the diagram)
- Issue channel access tokens v2.1 (Step 7 in the diagram)
The authentication method for issuing a channel access token v2.1 is in accordance with Using JWTs as Authorization Grants(RFC 7523)(opens new window). This is the Assertion Framework of OAuth Assertion Framework(RFC 7521)(opens new window) using JSON Web Token(RFC 7519)(opens new window).
# Create an Assertion Signing Key
Issuing an Assertion Signing Key is done in the these two steps:
# 1. Generate a key pair for the Assertion Signing Key
In order to generate a JWT, you must first generate a key pair (private key, public key) for the Assertion Signing Key.
# Assertion Signing Key specification
You can use a JSON Web Key(RFC7517)(opens new window) that meets these criteria as an Assertion Signing Key for JWT.
- Must be an RSA public key (
RSAis configured in thektyproperty). - RSA key length is 2048bit.
- RS256 (RSASSA-PKCS1-v1_5 with SHA256) is used in the signing algorithm (
RS256is configured in thealgproperty). - Must state that the public key will be used for signing (appropriate value configured in either
useorkey_ops).
Therefore, the public key of the Assertion Signing Key must contain these fields:
| Property | Description |
|---|---|
kty | Cryptographic algorithm family used in key. Specify RSA. |
alg | Algorithm used in key. Specify RS256. |
use | Use of key. Specify sig.*1 |
key_ops | Operation where key is expected to be used. Specify ['verify']. Exclude elements other than verify. *1 |
e | Absolute value for restoring public key. |
n | Cryptographic index for restoring public key. |
*1 Valid if one of either use or key_ops is specified.
kid is issued when a public key is registered in the LINE Developers Console. If the public key contains kid, an error will occur. Make sure the public key you are about to register doesn't contain kid.
The key pair for the Assertion Signing Key can be generated by the developer's own program based on the published specification, but it can be generated more easily by using a library that meets the specification.
Here are two examples of the steps to generate an Assertion Signing Key:
# Generate using Go language command line tools
You can generate a key pair using jwx command line tool(opens new window), which is a part of jwx(opens new window), an open source Go language library used for implementing JWT. Use these steps to issue an Assertion Signing Key.
# 1. Install jwx command line tool
To install the jwx command line tool, a Go language development environment is required beforehand. You can download the development environment from the Go language official site(opens new window).
Execute this command from the path where you installed Go to install the jwx command line tool.
# 2. Generate private key and public key
Use the same path to execute this command and generate a private key.
Use this command to generate a public key based on the private key.
If you succeed, a private key (private.key) and public key (public.key) will be generated as below.
private.key example:
public.key example:
# Generate using browser
If your browser supports Web Crypto API(opens new window), you can use the SubtleCrypto.generateKey()(opens new window) method to generate a private key and public key.
Enter this code on your web browser's developer console and execute.
If you succeed, the following private key (private.key) and public key (public.key) are generated.
private.key example:
public.key example:
# 2. Register public key and get kid
Select your channel from the channel settings on the LINE Developers Console and access the Basic settings tab. Next, click the Register public key button next to Assertion Signing Key and enter the public key generated in step 1. Click the Register button.
kid will be displayed if you succeed in registering your public key.
# Generate a JWT
You can use any JWT library(opens new window) or write your own code from scratch to generate a JWT from your Assertion Signing Key.
This is an example created using a JavaScript library introduced in JWT(opens new window). To use this code, you'll need to install these items:
The JWT is a string made up of a header, payload, and signature; all are required fields.
Header
| Property | Description |
|---|---|
alg | Fixed property: 'RS256' |
typ | Fixed property: 'JWT' |
kid | Use the kid property obtained in Create an Assertion Signing Key. |
This is an example of a decoded header value.
Payload
| Property | Type | Description |
|---|---|---|
iss | String | Channel ID. Found on the LINE Developers Console. Must be equal to sub. |
sub | String | Channel ID. Found on the LINE Developers Console. Must be equal to iss. |
aud | String | https://api.line.me/ |
exp | Number | The expiration time of the JWT. Set this value in UNIX timestamp. The max lifetime of a JWT Assertion is 30 minutes. |
token_exp | Number | Required when requesting a channel access token. This represents a valid expiration time for the channel access token in seconds. The max lifetime of a channel access token is 30 days. |
This is an example of a decoded payload value.
Signature
You can generate a JWT by signing the header and payload as shown above with your private key of your Assertion Signing Key.
This is an example of the code used to generate a JWT signed with a private key using node-jose. To create your own JWT with this code, change the privateKey to the value of the private key of your Assertion Signing Key and change the values of header and payload, respectively, and run it. See node-jose(opens new window) for more information on how to use node-jose. Be sure to sign with your private key to prove that the content has not been tampered with.
Example code using node-jose
Sign the base64url-encoded header, base64url-encoded claim set, and a secret key (such as an rsa_private.pem file) using the algorithm you defined in the header. The signature is then base64url-encoded, and the result is the JWT.
Example encoded JWT
# Issue channel access tokens v2.1
You can issue a channel access token v2.1 with the JWT assertion, generated by the procedure in Generate a JWT, specified.
- The response when issuing a channel access token v2.1 includes a channel access token and a unique key ID (
key_id) pair. To manage channel access tokens correctly, be sure to store the channel access token and key ID pair at the time of issuing. - The key ID is an identifier added to the Messaging API on June 22, 2020. If your app is using a channel access token v2.1 that doesn't have a key ID, we encourage you to re-issue a channel access token v2.1 and store the token and key ID pair. Change your app to always use the new token if the channel access token is re-issued.
- To issue a channel access token, specify the generated JWT and execute the Issue channel access token v2.1 endpoint.
- Channel access token and key ID are returned from the LINE Platform.
- Store the channel access token and key ID pair in a database or other location.
# Revoke channel access token v2.1
You can revoke a channel access token v2.1 with a valid channel access token specified.
Even if specifying an invalid channel access token and executing the Revoke channel access token v2.1 endpoint, no error occurs. To get key IDs paired to the current valid channel access tokens, execute the Get all valid channel access token key IDs v2.1 endpoint.To identify the valid access token, match the obtained key ID to its respective channel access token.
- Re-generate a JWT from the stored assertion signing key.
- Execute the Get all valid channel access token key IDs v2.1 endpoint with the JWT specified.
- The valid channel access token and key ID are returned from the LINE Platform.
- Explore the database that stores the channel access token and key ID pair.
- Search for the channel access token and key ID pair that match the obtained key ID.
- Get the valid channel access token.
- Specify the valid channel access token and execute the Revoke channel access token v2.1 endpoint.
- The channel access token is revoked from the LINE Platform.
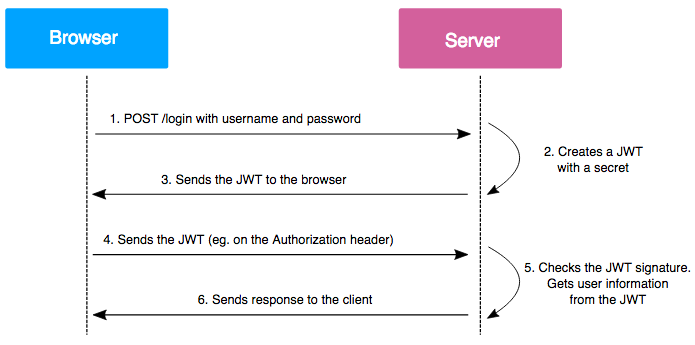
1. JWT Token Overview
JSON Web Token (JWT) is an open standard defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA or ECDSA.
Although JWTs can be encrypted to also provide secrecy between parties, we will focus on signed tokens. Signed tokens can verify the integrity of the claims contained within it, while encrypted tokens hide those claims from other parties. When tokens signs using public/private key pairs, the signature also certifies that only the party holding the private key is the one signed it.
1.1 What is JSON Web Token (JWT) Structure?
JWT tokens consist of 3 parts separated by a period ( . ).
These parts are:
- Header
- Payload
- Signature
The JWT typically looks like:
2. Setting up JJWT library
To start using JJWT library for JWT generation, add following dependencies in your build.gradle file.
Alternatively if using Maven, add following dependencies in pom.xml
3. Create JWT Token
Jwts.builder() is used to create a JWT token. We can specify claims, subject and other JWT attribute.
Generated JWT Token:
The above code to generate JWT is pretty self-explanatory however let’s check step by step how are we generating JWT token:
- Add claims
nameandemailwith valueJane Doeand[email protected]respectively - Add subject in JWT token with value
jane - Set Id for the JWT token using randomly generate GUID
- Set issued at to current time
- Set expiration to current time plus 5 minutes. So the JWT is valid for only 5 minutes
The JWT generated above is not signed (Check algorithm alg attribute in the header). We have just encoded the claims in JSON format. If using JWT for authentication or authorization it is advisable to Sign the JWT, so it can be verified.
4. Validate/Parse JWT Token
To validate or parse the JWT token, Jwts.parserBuilder() method is used.
While parsing the JWT token we need to pass Signing key to verify the JWT signature. Let us see how to sign the JWT token using different algorithms.
5. Create and Validate JWT Token Signed using HMAC Secret
The simplest way of creating a signed JWT token is by using HMAC secret. HMAC stands for hash-based message authentication code and is cryptographic hash function. It is used to simultaneously verify both the data integrity and the authenticity of a token.
5.1 Create JWT Token signed with HMAC
To create JWT token signed with HMAC shared secret, we need to specify signature using .signWith() method.
Generated JWT Token:
5.2 Validate/Parse JWT Token signed with HMAC
To validate/parse the JWT token generated using HMAC shared secret, the same steps can be applied. We need to use setSigningKey() method to set the key before we parse the JWT token.
Output:
If the JWT token expires (exp claim value is less than current system time), the parseClaimsJws() method will throw SignatureException.
6. Create and Validate JWT Token Signed using RSA Private Key
When using JWT token for microservice authentication/authorization it is advisable to sign with RSA Private/Public Keys instead of using Shared HMAC Secret. The token is generated and signed by a central authority (usually an Authorization Server) and each microservice can validate the JWT token using the Public Key exposed from Authorization Server.
Before we see how to generate JWT token with Private/Public key, let us see how to generate a Private and Public RSA Key pairs.

Generate Jwt Token With Private Key
6.1 Generate Private and Public RSA Key
Generate an RSA private key, of size 2048, and output it to a file named key.pem:
Extract the public key from the key pair, which can be used in a certificate:
The key.pem file contains the private key generated using RSA and public.pem file contains public key.
6.2 Create JWT Token signed with RSA
Following code snippets shows how to generate JWT Token Signed using RSA.
Generate Jwt Token With Private Key Python
Generated JWT Token:
For simplicity the Private Key is hard coded in above example. However, in real production system it will be loaded from environment variable, or a secret vault (Hashicorp Vault or AWS Parameter Store).
In above example the method getPrivateKey() gets the java.security.PrivateKey which is then used in Jwts.builder to sign the JWT token using Private key.
6.3 Validate/Parse JWT Token signed with RSA Private/Public Keys
Next, let us validate and parse the JWT signed using RSA. For that we will need Public Key instance in java.security.PublicKey format which Jwts.parserBuilder will use to validate the JWT.
Output:
In above example, we have hardcoded the Public Key. In a production system, it is usually configured through environment variable or service configuration.
7. Source Code – Generate and Validate JWT Tokens using Java & JJWT
Source code for the Creating and Validating JWT token in Java.
Github – source code